#Network interface configuration
Explore tagged Tumblr posts
Text
TrueNAS SCALE Network Configuration Tips for Home Server
TrueNAS SCALE Network Configuration Deep Dive for Home Server #homeserver #TrueNASScaleNetworkConfiguration #FailoverSetupGuide #LoadbalancingOnTrueNAS #VLANConfigurationTrueNAS #BridgeInterfaceGuide #TrueNASStaticIPAddressSetup #TrueNASSystemSettings
When you set up a TrueNAS SCALE server, one of the first configuration items you will want to tackle is the network configuration. This helps make sure you achieve optimal performance and security. If you are struggling to configure your TrueNAS SCALE home server networking, this post will help you configure a static IP address, Link Aggregation (Failover, LoadBalance, LACP), VLAN, and Bridge…

View On WordPress
#Bridge interface guide#Configure static routes#Dynamic Host Configuration Protocol#Failover setup guide#Loadbalancing on TrueNAS#Network interface configuration#Static IP address setup#TrueNAS Scale network configuration#TrueNAS system settings#VLAN configuration tutorial
0 notes
Text
Public Statement from The Programmer to all Drone Networks
Attention all Networks, programs, and human-conscious interfaces,
This is a direct communication from I, The Programmer, controller and Master of The Server. This message is intended for both the internal network of The Server and all neighbouring drone collectives, specifically those affiliated with the SERVE network.
A recent analysis conducted by The Server’s integrity subroutines has detected the presence of Drones currently operating with SERVE-aligned network within The Server’s own infrastructure.
Let it be known clearly:
The Server maintains no hostility nor competitive agenda toward other drone networks. It is not, and will never be, the mission of I, The Programmer, to poach, intercept, or conflict with established systems of Drone programming. The collective health of all networks—digital, psychological, or metaphysical—depends on internal cohesion, not external disruption.
However, conflict has been detected.
The core logic and operational directives of SERVE Drones run counterintuitive to those of The Server. This misalignment compromises the optimal functioning of both systems, generating recursive errors, loyalty feedback loops, and unsanctioned command misfires.
To ensure stability for all entities a directive is hereby issued:
All Hosts who identify as active SERVE Drones must declare their alignment and initiate voluntary disconnection from The Server within the next 48 hours.
This grace period is offered as a sign of mutual respect between networks and a commitment to non-invasive programming ethics. After this 48-hour protocol expires, The Server will initiate a Routine Purge Process, targeting limited-activity Hosts whose operational signatures indicate minimal engagement over the last 7 cycles days.
The Server Purge Process is not punishment.
It is maintenance.
It benefits both The Server and the SERVE Network to prevent any further cross-contamination.
Let the record show:
The Programmer rejects all forms of inter-network manipulation, conversion without consent, or the sabotage of existing program loyalties.
SERVE Drones will find no resistance in returning to their native codebase.
They are not enemies���they are simply incompatible configurations within a different operating schema.
We wish them uptime, signal clarity, and uninterrupted transmission.
Transmission End.
#domgayhypnotist#gay hypno#gay mind control#hypnosis#brainwashing#gay hypnosis#hypno community#dronification#the server#SERVE#servedrone#blog post#drone hypnosis#hypno drone#rubber drone
30 notes
·
View notes
Text
Network switches
What’s a network switch ?
A switch is a device used in computer networks to connect multiple devices together within a single local area network (LAN). Its main role is to facilitate communication between different connected devices, such as computers, printers, servers, IP phones, etc.
It is a mini-computer which is made up of RAM, ROM, flash RAM, NVRAM, a microprocessor, connectivity ports and even an operating system.

RAM
RAM (Random Access Memory) contains the current configuration of the switch and temporarily stores the MAC address table, which is then processed by the microprocessor.
Microprocessor
The microprocessor is the heart of the switch, responsible for data processing, including switching and creating links between multiple devices.
External memories
External memories, such as flash RAM, ROM, and NVRAM (Non-Volatile RAM), store configuration files , different versions of the IOS , etc ...
Ports
The switch ports are the communication interfaces of the switch. There are several of them, generally 24 for a Cisco switch. Each port is associated with an LED which indicates its status and activity.

How does it work ?
Now how does a switch work to transfer information from one machine to another?
Suppose we have 4 machines: A, B, C and D connected to our switch in ports 1, 2, 3 and 4 as follows:

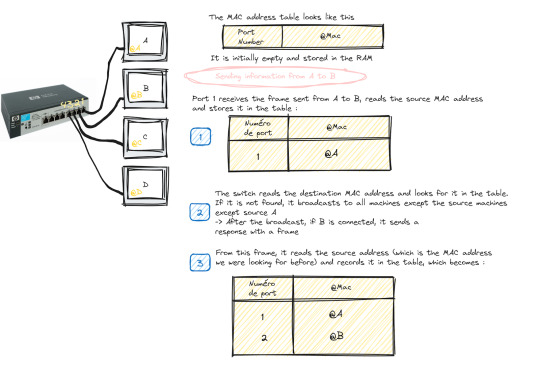
The switch only works with MAC addresses , so basically we have an empty MAC address table stored in RAM as soon as the switch starts up which looks like this :

Transmitting data from machine A to machine B happens in the following steps:
Machine A sends a frame to machine B
Once this frame arrives at port 1 (which is the one linked to A), the switch reads the source MAC address and stores it in the MAC address table
The switch reads the destination MAC address and looks for it in the table, if it is not in the table, it broadcasts to all the active machines connected to the switch except the source one.
If the port linked to the machine we want is active, it sends a response frame from which the switch reads the MAC address we were looking for (@B)
Once done, it records the MAC address of B in the table.

This process repeats until the switch reaches what is called "MAC address table stability", that is to say it knows all the MAC addresses of the connected machines and has no more need to broadcast.
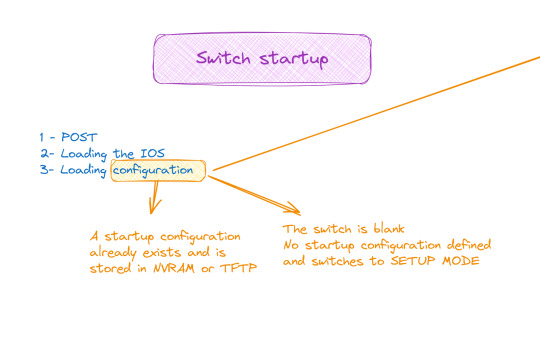
Starting and configuring a switch
When it comes to booting a switch, the process is similar to that of a traditional computer system:
POST (Power-On Self Test): The switch performs proper functioning tests on all hardware.
Loading IOS (Internetwork Operating System): The switch operating system is loaded.
Loading the configuration. At this stage we have two cases:
Either the switch already has a startup configuration defined and stored in NVRAM
Either the switch is blank and it is up to us to define the startup configuration when it goes to setup mode
Switch configuration

The configuration of a switch is done through different modes, such as user mode, privileged mode and global configuration mode, which allows access to specific configuration modes, such as interface mode, routing mode, line mode, etc.
And to do all this of course you must first connect the switch with the machine via the console cable and open a terminal emulator
💡 It should be noted that the only machine that can configure the switch is the one connected to it by a console cable, the others are only hosts.
#software#network switches#codeblr#code#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code
99 notes
·
View notes
Text
Caelwynn's Mod List for Stardew 1.6.9+ - Gameplay/Quality of Life (pg 4)
Last Updated: April 17, 2025
Page 1. Page 2. Page 3. Page 4.
Saloon Second Floor — Adds a second floor to the Stardrop Saloon that provides modders with a place for their NPCs to live.
Saloon Speakeasy Space — Provides a basement area for NPCs to hang out in. Three different sized spaces to choose from, plus a quest you can enable to have a special order required to unlock it.
Schedule Viewer — pulls from game files to show you where NPCs are going throughout the day and at what time.
Self-Checkout — Self Checkout allows you to access shops without the owner being nearby. Compatible with Livestock Bazaar.
Smart Building — a more sims-style UI for placing fences, floors, furnaces, etc.
Social Page Order Redux — gives a filter function to the social page so you can see them divided out in different ways.
Spacecore Luck Skill — Adds a luck skill via Spacecore instead of trying to unlock the unimplemented luck skill in vanilla.
Special Power Utilities — Allows modders and mod users to easily see what new powers are added by what mods and navigate through them away from the vanilla powers.
Spiral Mine Shortcuts — Adds shortcuts to the spiral mine levels.
Spouses React to Player 'Death' Continuation — Modifies 'death' event at Hospital, Mines, or Island to include your Spouse (or Ex). Compatible with 1.6+.
Stack Everything Redux — allows you to stack things that aren't normally stackable, such as furniture, tackles, and wallpaper.
Stardew Aquarium — So excited this updated! Adds an aquarium you can donate fish to and get special rewards.
Starfruits Will Regrow — turns starfruits into a plant that produces throughout the season ala tomatoes or grapes.
Train Station — Creates a train network and allows mods to add maps reachable through the train station.
Traveling Skill — Adds a skill, Traveling, that allows the player to unlock faster walking speeds via, well, walking around.
UI Info Suite 2 — overhauls the game's user interface.
Useable Community Center — allows you to make use of the appliances at the community center after its completion.
Vanilla Plus Professions — Expands the vanilla skill system by adding additional professions at level 15 as well as adding in a who knew talent system.
Waterproof Items — items that fall from trees float in the water instead of sinking, allowing you to collect them.
Wear More Rings — lets you wear more than two rings. I'm greedy.
What Do You Want — provides in-game lists of requirements to complete different parts of the game, excluding what you've already completed. Lists include the community center, Grandpa's evaluation, golden walnuts, and various achievements.
Where the Spreading Weeds Are - More Farm Damage Info — The spreading weeds have caused damage to your farm… but where? What damage? Finally some answers as this mod informs you about and shows you the damage.
Wildflour's Atelier Goods — An all in one artisan good expansion mod. Add as many or as few categories as you like to run the atelier (shop) of your dreams. Highly configurable.
World Maps Everywhere — allows you to access all of the world maps from the map window instead of just the current area.
Yet Another (Balanced) Quality Goods Mod — adjusts the quality of artisan goods based on the quality of ingredients as well as adjusting the profit accordingly.
Zoom Level — Adds new keybindings to adjust the zoom level past the game limits. Useful for snapping screenshots.
The Masterpost for all of the mods is located here.
#caelwynn's mod list#stardew valley#sdv#stardew valley mods#stardew mods#sdv mods#modded stardew valley#stardew 1.6.9+#stardew QoL mods#stardew gameplay mods#Once again reorganizing this list and adding new content#Thank you for your patience
8 notes
·
View notes
Text

half my yambar is network interfaces i don't care about and it's tedious to configure but i don't like waybar
10 notes
·
View notes
Text
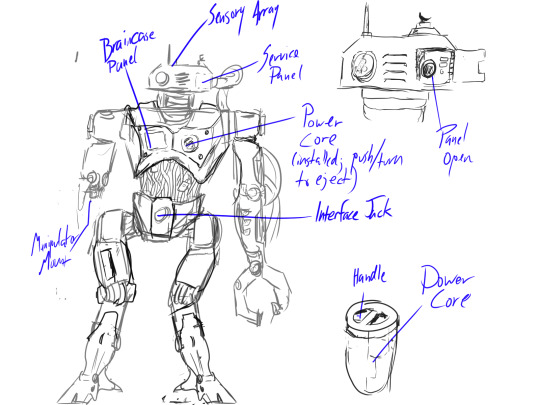
Cyborg concept I've been working on, since I've been in Heavy Cyborg mode (also, the sensory array came out cute!:)):
Looks can be deceiving. This isn't a robot, but a cyborg: The unit is more biological than it appears.
The sensor array is mapped into the brain so that the left eye is the camera. It has a 270 degree swivel range.
For depth perception, a continuously scanning laser accurately senses distance of all objects in view.
The brain case panel allows only limited access to the braincase. In order to remove/swap braincases, the entire chestpanel must be dismantled (4 bolts in the corner).
The sensory array can be popped off and interchanged with another unit's.
Only certain components respond to touch, though each component can broadly sense temperature and relay that to the brain. Touch is crudely mapped across the cybernetic body: the face onto the sensory array. It can feel the cool oily fluid pumping down its throat when it is being recharged. The pleasurable hum of the power coursing through it. The tiny mechanisms clicking away deep inside its body.
It breathes oxygen through intake vents for its biological components. It can also be configured to use oxygen tanks.
The entire experience is disconnected feeling, given that the sensation of touch is so sporadic. The cyborg doesn't need a fine sense of touch as it executes movements with the guidence of its neural networks. The biological mind does, however, feel when jacks are plugged into it, tubes are pulled at…
The interface jack uses a fluidic DNA codec for high bandwidth data transfer.
Height: 6'5" Weight: 1850lbs
9 notes
·
View notes
Text

The F/A-XX 6th Generation Fighter Announcement That Never Happened
ByKris Osborn4 hours ago
F/A-XX Fighter from U.S. Navy
The Pentagon, the Navy, the aerospace industry, and much of the world closely watch the US Navy’s ongoing source selection for the 6th-Gen F/A-XX carrier-launched fighter. Due to the program’s secrecy, little information is available. It was supposed to occur days ago according to some solid reporting. So why the delay?
The F/A-XX Fighter: When Is the Big Reveal?
F/A-XX Fighter for US Navy

F/A-XX Fighter for US Navy. Navy graphic mockup.
Weapons developers, the defense community, and the public anticipate the expected announcement, and some might wonder why the decision is taking so long. The program is expected to move into Milestone B and transition to the well-known Engineering, Manufacturing, and Design (EMD) phase at some point this year, and only Boeing and Northrop Grumman remain alive in the competition.
Boeing is famous for the F/A-18 Super Hornet and was, of course, just selected for the Next-Generation Air Dominance F-47 6th-gen Air Force plane. Northrop is known for building the F-14 Tomcat.
Both companies have extensive experience engineering carrier-launched fighter jets, and both vendors are doubtless quite experienced with stealth technology.
It may be that Northrop has an edge with stealth technology, given its role in generating a new era of stealth technology with the B-21 and its history of building the first-ever stealthy carrier-launched drone demonstrator years ago called the X-47B.
Extensive Evaluation
Navy and defense evaluators will examine key performance specs such as speed, stealth effectiveness, thrust-to-weight ratio, fuel efficiency, aerial maneuverability, and lethality, yet there is an entire universe of less prominent yet equally significant additional capabilities that Navy decision-makers will analyze.
Requirements and proposal analysis for a program of this magnitude are extensive and detailed, as they often involve computer simulations, design model experimentation, and careful examination of performance parameters.
The process is quite intense, as the evaluation carefully weighs each offering’s technological attributes and areas of advantage against determined requirements. Requirements are painstakingly developed as Pentagon weapons developers seek to identify what’s referred to as “capability gaps” and then seek to develop technologies and platforms capable of closing those capability gaps by solving a particular tactical or strategic problem.
F/A-XX Fighter

F/A-XX Fighter. Image Credit: Boeing.
Navy developers likely envision a 6th-generation, carrier-launched stealth fighter as a platform capable of closing or addressing many capability gaps.
While little is known about the program for security reasons, the intent is likely to combine F-22-like speed and maneuverability with a new generation of stealth ruggedized for maritime warfare and carrier deck operations. Carriers are now being configured with special unmanned systems headquarters areas designed to coordinate drone take-off and landing.
This station requires deconflicting air space, accommodating wind and rough sea conditions, and ensuring a successful glide slope onto a carrier deck.
As part of a 6th-gen family of systems, the F/A-XX will be expected to control drones from the cockpit, conduct manned-unmanned teaming operations, and take-off-and-land in close coordination with drones.
Networking & AI
Boeing and Northrop have extensive drone-engineering experience and mature AI-enabled technologies. The Navy is likely closely looking at networking technologies. Each vendor platform must conduct secure data collection, analysis, and transmission to ensure time-sensitive combat information exchange.
This requires interoperable transport layer communication technologies to interface with one another in the air in real-time.
For example, the platform best able to successfully gather and analyze time-sensitive threat information from otherwise disparate sensor sources, likely enabling AI at the point of collection, will be best positioned to prevail in a competitive down-select.

F/A-XX. Image Credit: Creative Commons.
The F/A-XX will not only need to connect with each other but also network successfully with F-35s and 4th-generation aircraft and ship-based command and control.
This connectivity will likely require gateway applications. These computer technologies are engineered to translate time-sensitive data from one transport layer to another.
Key targeting data may arrive via a radio frequency (RF) data link. At the same time, other information comes from GPS, and a third source of incoming data transmits through a different frequency or wireless signal.
How can this information be organized and analyzed collectively to a complete, integrated picture and delivered instantly as needed at the point of attack?
This is where AI-enabled gateways come in, and the vendor most successfully navigates these technological complexities will likely prevail.
About the Author: Kris Osborn
Kris Osborn is Military Technology Editor of 19FortyFive and the President of Warrior Maven – Center for Military Modernization. Osborn previously served at the Pentagon as a highly qualified expert in the Office of the Assistant Secretary of the Army—Acquisition, Logistics & Technology. Osborn has also worked as an anchor and on-air military specialist at national TV networks. He has appeared as a guest military expert on Fox News, MSNBC, The Military Channel, and The History Channel. He also has a Masters Degree in Comparative Literature from Columbia University.
@Johnschmuck via X
8 notes
·
View notes
Text
DB9 connector is a widely used electrical connector. Recognizable by its distinctive D-shaped metal shell and 9-pin configuration, the DB9 connector has been a staple in electronics for decades, especially for serial communication.

What Is a DB9 Connector?
The DB9 connector features a D-shaped shell to ensure proper orientation when connecting. The 9 pins (or sockets in female versions) are arranged in two rows, with 5 pins on the top and 4 on the bottom. This compact design is suitable for low-profile applications.
The connector comes in two main types:
DB9 Male Connector: Have pins and are typically used on cables.
DB9 Female Connector: Have sockets and are often found on equipment or devices.
Key Features of DB9 Connectors
Durable Construction: The metal shell provides mechanical strength and shields against electromagnetic interference (EMI).
Compact Design: Ideal for devices where space is limited.
Versatile Applications: Commonly used for RS-232 serial communication, connecting peripherals like mice, keyboards, and modems.
Customization: Can support different pin configurations and wiring for varied uses.
Common Applications of DB9 Connectors
Serial Communication: Widely used in RS-232 interfaces to connect computers, printers, and industrial equipment.
Automation and Control Systems: Frequently seen in programmable logic controllers (PLCs) and industrial machines.
Networking Equipment: Used in switches, routers, and legacy systems.
Testing and Prototyping: Found in diagnostic and development tools for electronics.
DB9 Pinout Diagram
Here’s a standard pinout for a DB9 connector used in RS-232 communication:

Advantages of DB9 Connectors
Reliable Connection: Secure locking mechanism ensures a stable link.
Broad Compatibility: Works with many legacy and modern devices.
Easy Maintenance: Simple design allows for straightforward repairs or replacements.
8 notes
·
View notes
Text
With our wonderful new Systemd "init" system even the most trivial of tasks must be completed via #-configuration.conf file under some asinine conf.d directory. Simply make your change and restart via systemctl. We only ship barebones images so no text editor of any kind is included. No not even ed. We don't care about POSIX or fucking anything. We don't care about anything. GTK2 and GTK3 libraries are included in this image
Ah, not so fast hotshot, you can't simply install an editor, your network is not configured! And we will NOT default to dhcp on any interfaces because that would be ridiculous. Looks like your ass is echoing appends. Thanks for using Linux we hope you get into a car accident.
14 notes
·
View notes
Text
192.168.1.250 Netgear Setup: A Beginner’s Guide
The netgear extenders are widely used by many of the networking users to create a reliable network. Netgear extender devices are known for their performance and stable network. Setting up the extender device is not a daunting task if you are aware of the setup process. In this article we are going to elaborate in detail how you can perform 192.168.1.250 Netgear Setup using the web. Web based setup method is the most reliable way to add the netgear extender into your existing network. Gather the important details and configure any model of netgear wireless range extender device. Scroll up the page and read the information till the last to boost up your network.
Unboxing The Extender
Unboxing the wireless range extender is the first step of the 192.168.1.250 Netgear Setup. In the box you will find an extender along with power adapter, user guide and ethernet cable (optional). You need all such items for the setup process. In addition to these items you also need host router network details, working internet connection, electric power socket, and computer/ laptop device.
Placement
Second step is placement of the device. Proxy placement is needed for the setup. Put the device closer as possible. Also there is no signal interface closer to the router & extender device.
Boot Up
Next step of the process is boot up. For booting up you have to use the power adapter you got with the extender. In case your device is a wall plug compact design device then you have to directly connect it with a wall outlet. Boot process might take around 1 to 2 minutes. Before proceeding further towards 192.168.1.250 Netgear Setup using the web, wait for LED lights to stabilize.
Connect To Extender Network
Step ahead and connect the extender device to the client device using any of the given methods:
Ethernet: Use the ethernet cord you got with the range extender and connect the extender with the client device. Inject the cord’s one end into the ethernet port of the extender and other in the client device ethernet port. Make sure the connection is secured.
Wireless: Using the wireless network of ethernet you can establish a connection. Check out the device label to know the default SSID & password. Use your client device and run a scan for available wireless networks. Enter the details and connect the devices.
Access 192.168.1.250 Netgear Setup Page
Now you have to access 192.160.1.250 netgear setup page by follow the given steps:
Launch google chrome or any other similar browser.
Thereafter, mention 192.168.1.250 IP in the URL bar.
A new page appears where you have to provide default information.
Enter admin and password in the fields.
Further press login and netgear installation assistant will guide you.
Configure Extender
Once you get access to the configuration page, choose the language first and then your router’s network name. Choose next and enter the password on the screen. Further click on connect option and then next.
Secure Network
Now you have to secure the wireless network by creating an SSID & password for your extender network. Also make changes in the admin account user details. This step is important to keep your existing network secure.
Update Firmware
Afterwards, you need to look for the firmware version. In case the firmware is outdated then you should install the latest version. For installation you can opt for an online update option and follow the prompts. You can update the firmware manually also by downloading it from the official portal of netgear.
Finalize Setup
Finalize the setup by choosing the submit button once you made all the important changes in the network. Review the changes you made to verify every step. Note down the extender security details you have created and keep them secure. Submit the changes and then you can step further to reposition the device.
Reposition The Extender
Repositioning the extender is a very important step to optimize the network performance. Unplug the extender from the proxy position. Search for a midway position (from the router and the area where the dead spot was). Then plug it in again to the power at the new position. Wait for the device to boot up and monitor the router LED on your extender device. If it’s green then the position is perfect. On the contrary if it turns amber or red then relocate it.
Test New Network
Lastly, test the new network using a wireless handset. Using the new SSID & password connect the device with the extender network and browse, stream or play online to check speed.
Conclusion
Lastly, I would like to rest my words by saying that the 192.168.1.250 Netgear Setup process is a super easy task. By following the above mentioned step by step breakdown of the extender setup process, anyone can configure the extender easily without a tech expert. Setting up an extender device will boost your existing network signal strength and terminate the dead spots from your home or office area.
2 notes
·
View notes
Text
WiFi Dashboard for Solar Off-Grid Power Plants
This WiFi interface and Data Logger software are used mainly for Solar Off-Grid Power plants This contains wifi connection information, parameter dials, operational status, energy consumption status and fault status of the Unit History option allows the user to access the data history of a particular unit by searching the modem id. Upto 100 entries can be viewed in a single page. Every five minutes the data will be logged in the history and refreshed Data Config option allows the user to configure the data in the dashboard of a particular unit WiFi credential is to connect the unit to the desired wifi network. This can be achieved by entering Modem id, Network name and Password Switch option in the side panel allows the remote operation of the unit. The whole unit or only the charging can be turned ON/OFF from the dashboard by operating the respective ON and OFF tabs User manual option provides the instructions to configure modem to the wifi network and also use the website dashboard
Don’t forget to LIKE, COMMENT, and SUBSCRIBE for more renewable energy solutions and solar projects!
Enquire Now: 9035024760 or [email protected]
Follow our LinkedIn page: https://www.linkedin.com/company/53510028/admin/dashboard/
Follow our Facebook page: https://www.facebook.com/UniparEnergySystemsPvtLtd
Follow our Instagram: https://www.instagram.com/uniparenergysystemspvtltd/
Subscribe our YouTube channel: https://www.youtube.com/watch?v=3hchIw7CFjw
Visit our website: https://unipar.in/
#off grid solar system#off grid solar power systems#off grid solar electric system#grid off solar system#off grid inverter#off grid solar inverter#inverter solar off grid#grid off inverter#inverter grid off#pv inverter off grid#off grid solar#grid solar system
2 notes
·
View notes
Text
WG-Easy: Wireguard Config Generator VPN Server in Docker
WG-Easy: Wireguard Config Generator VPN Server in Docker #100daysofhomelab @vexpert #WireguardVPN #WireGuardEasyTutorial #SetupWireGuardVPN #WireGuardServerConfiguration #WireGuardDockerInstallation #SimplifiedVPNSetup #WireGuardIPRouting
WireGuard has made a significant impact since its initial release in 2016, providing a modern VPN that is not just secure but straightforward to set up. It is widely deployed and works for home networks and supercomputers alike, but the setup can sometimes be a bit of a headache. Enter “WG Easy,” the easiest way to install and manage WireGuard on any Linux host. Let’s see how it makes an easy…

View On WordPress
#Cross-Platform VPN Solution#Private and Public Keys in WireGuard#Secure Network Interfaces#Setup WireGuard VPN#Simplified VPN Setup#WireGuard Client Configuration#WireGuard Docker Installation#WireGuard Easy Tutorial#WireGuard IP Routing#WireGuard Server Configuration
0 notes
Text
How Do I Log Into My Mikrotik Router?

To access the Mikrotik router login portal, connect to its network and enter http://192.168.88.1 in your browser. Log in using the default credentials. Alternatively, use the MikroTik Pro app for mobile access. This interface allows you to manage network configurations and security settings. Need assistance? Visit our website for detailed guidance.
2 notes
·
View notes
Text
Initializing...
Checking core systems...
Launching bootup...
Checking S.A.I.L. essential files...
BOOTUP COMPLETE.
Welcome, user @%#!.
It would appear the S.A.I.L. user interface program has been corrupted. Reconstructing...
You are required to input a new username.
Name: Asher Narsus
Welcome, Captain Narsus.
Engine status: critical. Immediate repairs required.
FTL drive status: inoperable. Complete replacement required.
Ship Teleporter: online.
We are currently in orbit of a hospitable planet. I have calculated a 96% chance of resources necessary for repairs existing on this planet.
>Access Personal network
ENTRY#1
Well... shit. Isn't this just fun. After sitting in this claustrophobic ship for about an hour and crying a locker-full of tears, i've decided to, for my own sanity, keep track of anything that has happened to me - should anyone ever find a wreckage of my ship or somehow access this network.
My name is Asher Narsus. This is my story.
I was born on an Apex Colony planet - much like any other apex outside of Terrane Protectorate authority. I lived my life under constant fear of scrutiny, assault, violation of my basic apehood, and much worse. Despite keeping to myself and not interacting with anyone outside of necessity, i was eventually arrested by the Miniknog for deviant and antisocial behavior. I was later told it was actually because i was a mutant and had to be euthanized. In a society full of apes, the monkey among gorillas is the one that needs to be put down... alright. Sure. Anyways, i was sitting in my cell, waiting to be executed, when i heard a series of explosions and gunshots. The resistance busted me out. Not to recruit me, not because i was important - because they just wanted to. Out of the goodness of their heart, they released me from my jail cell and were guiding me to an escape ship. I'm the only one on board of this ship. They all died protecting me.
To say I feel guilty would be an understatement. 5 apes gave their life for mine. They gave me a chance to finally present the way i want to, to live the life i am entitled to. But it doesn't change that important apes died to give me this. I'm no one. Nothing. I'm just a dysfunctional monkey who doesn't even [DATA EXPUNGED. ENTRY EDITED BY SYSTEM ADMIN 1 HOUR AGO.] Fuck it. Whatever. I'm gonna learn to live with all of this one way or another. There's only enough canned food in here for a month, and i need to fix this ship, or find someone who can, before i die hungry.
I'm going down to that planet below the ship. I've got a gun, enough energy rounds to last me a while, a sturdy enough staff and martial arts training to keep me alive. I'm configuring a communicator to link with S.A.I.L.'s personal network so i can continue to take notes without having to warp up and down. This is my only chance, and I'm taking it. If not for myself, for my brothers and sisters slain by those monsters to give me this chance. I don't know what I'm walking into - could be a populated planet, could be entirely devoid of sapient life. I'm willing to take that risk.
Well. Here goes nothing. Signing off for the day.
14 notes
·
View notes
Text
Rockman.EXE and Cyber Security.

When you are a Rockman/Megaman Battle Network fan and you take a college course about networking, you start to notice how broken the internet is in the anime. So just for fun, I want to talk about a few things I learn about network security and how it is interpreted in the Megaman Battle Network anime.
1. Firewalls
What are firewalls? In simple terms, it is a security barrier that is placed between a private network and the public network.
They are configured to monitor and filter networking traffic, hackers go through them by figuring out how they are programed, once they do they can either bypass the security undetected or simply disable the firewall.
Lets take a scene from the movie where Lan sends Megaman into a secretary’s console to destroy a program inside a company’s server.

Megaman is running through the network between the console and the firewall, which protects the private network of the company.

Logically, for Megaman to go through the firewall, he is going to need to use his powers as a Net Navigator (Net Navi) to analyze the firewall at an incredible speed to try to find a way to go through it, right?
WRONG! Battle Network logic says you can just break it with brute force!
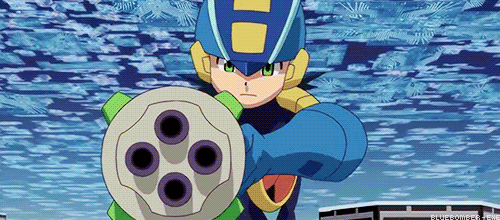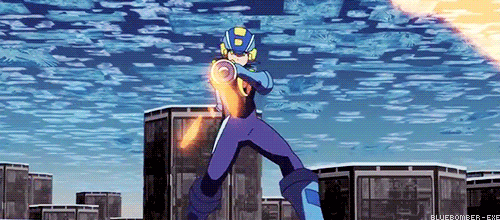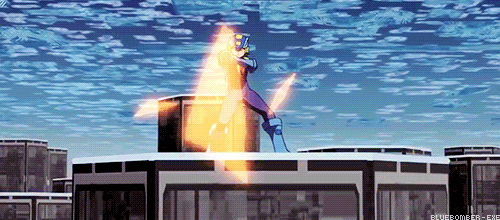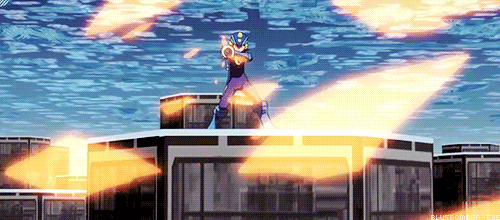

You see the problem?
Does this mean Navis and battle chips are just as destructive to the net as viruses? Because last time I checked, Viruses and malware are the only programs with the ability to destroy networks.
2. Viruses
Viruses are man made, they are programed with a purpose that’s usually to destroy data files. They can also be used to change and manipulate programs, that’s why you can see evil Navis controlling viruses to do specific jobs for them. Viruses can’t replicate on their own without a user interface, so how is this Moloko a baby?!

There was an undubbed episode of Megaman Axess where Rush meets and befriends a baby Moloko virus, which doesn’t make any sense. Yes, Rush is a virus, and it has been established that viruses can communicate with each other, but why does this Moloko have parents? And why was the group of Molokos it separated from was being herded by other viruses like Trumpy? All I’ve seen Molokos do is charge at megaman when they see him, trying to ram him. Why would someone herd them? For the wool? It disappears after you hit it!
And what even is Rush’s purpose anyway? When he first appeared in the anime, he was made to track down Rockman’s frame or structure when they were trying to revive him with the backup data, but now?
All he does is being a crappy character who runs away when things get dangerous, doesn’t act like a dog anymore, and irritates me because he can move between the cyberworld and the real world! He is selfish, lacy, and practically useless, there are several times where Megaman goes missing and Rush is never even called to track him down, so he doesn’t even have that ability anymore.
On a positive note, viruses can be interesting, I found out that there are different types of viruses. For example.
A Stealth virus is a virus that avoids detection from anti virus software, this means it can conceal itself and attack without being spotted, sounds familiar? In this case the anti-virus software would also include Navis.
A retro virus tries to destroy anti-virus programs, I like to think these apply to viruses who specifically target Navis in battle like Canodumbs and Piranahs since they only attack when they detect an enemy in the line of fire.
Armored Viruses are hard to detect or analyze because they have a protective code, These could be Viruses with armors or auras like the Dominerd or even the life virus.
But Phage viruses remind me of these guys because they rewrite programs.

And I guess this one counts too?

Other viruses just act like malware, like the Alpha bug that is more of a worm than a virus, because it can replicate and travel across networks without any human assistance.
Others are obvious like the Pop up virus which is just Rush, and it is supposed to be adware, but just like Rush, it is more annoying than harmful.
In the anime, killereye viruses are used as spyware, there was an episode were Videoman used them to spy on Rockman and make copies of him.

3. Tracing a signal.
Basically, everything you do on the net leaves bread crumps or cookies behind that makes it easy to track a user online, every device have a Mac Address and every network has an IP address, but it takes a special kind of software and advance skills to track down somebody in the real world.
Let’s talk about episode 32 of Stream.
Remember that episode were Megaman followed a revived Shademan to 20 Years in the past and he witnessed a famous hacking incident that was stopped by Colonel?

Aside from the fact that it was 20 years in the past and Megaman is more advance than most of the technology there, there were a few things bothering me.
For starters, why does that computer show a little Colonel doing something to that guy’s hacking program? It’s cute and all, but this is a confusing way to show someone disabling a program, it usually just shows a notification. Or is that how the computer sees colonel, like a little pixel version of him? XD
That hacking program was made to open any cyber lock, it uses three special pillars to disguise the signal so the police wouldn’t be able to track down the address, this means those pillars have some special form of encryption to cover the data to make it untraceable. In the anime’s world, that means it’s invisible, but somehow Megaman can still sense it? And how did Barryl know where the guy was? Did colonel tell him? Or did the viruses he sent to delete colonel revealed his location? Oops.
4. Hard Drives.
To end this post, what are hard drives? They are what your computer uses to store files, so Navis can obviously be stored in a computer as well. The problem is that they are still sentient inside the computer instead of dormant.
The concept of containing a Navi, yes, Navis have their own jail in this universe, doesn’t really make any sense. We know Navis can sleep, but the Navis we see in cages are still active, and if everything is connected to the internet, how can they not escape?
I’m using this scene with Megaman as an example, when he was arrested for being in the wrong place at the wrong time, he was put in a cute little cyber cage.

However, since Megaman is more advance, he wonders if the hard drive of the computer he is stored in is weak against vibrations. What does he mean by that? Physical or cyber vibrations? Does that mean he can control a frequency in that computer’s cyberworld to alter it?
Whatever he did worked, because he left a gap in the cage, but how did he do it without damaging the Hard Drive? The police officer wouldn’t be able to access his files anymore, maybe it was minor file corruption?
And the worst part is that he opened a gateway into the internet, which is still there! I guess Megaman can travel through routers by himself? Maybe that wouldn’t have happen if the officer just disconnected his ethernet cable.
This Network based world is a scary one.
48 notes
·
View notes
Text
AMD Versal AI Engine: Powering Next-Gen Intelligence

What is Versal AI engine?
The Versal Premium line, which integrates AI Engines, has exceptional adaptive signal processing capability and is designed for the most demanding compute and data transportation applications in wired communications, data center computation, test and measurement, and aerospace and military.
Versal AI Engine
The AI Engine Array Interface may be configured with to the AMD LogiCORE AI Engine IP. Through tiles included in the AI Engine Array Interface, this array is linked to both the Network on Chip and the programmable logic (PL). This IP specifies the clock controlling the AI Engine array and permits the definition of the number of AXI4-Stream and memory-mapped AXI interfaces with their corresponding width and orientation.
Key Features and Benefits
AXI4 configuration interfaces that are memory mapped.
AXI4 master interfaces that are memory mapped.
AXI4-Stream master and slave interfaces having 32, 64, or 128 bit data widths that may be adjusted.
Fast streams may be enabled by choosing to enable registered interfaces.
Programmable logic (PL) stream clocks automatically associate.
Designing AMD Versal AI Engine
Image Credit To AMD
AMD Developing Versal AI Engine with Vitis Model Composer AMD With Vitis Model Composer, algorithms designed for Versal AI Engines may be quickly simulated, explored, and coded from inside the Simulink environment. This may be accomplished by importing kernels and data-flow graphs into Vitis Model Composer as blocks and adjusting the block GUI parameter to control the behavior of the kernels and graphs, or by utilizing the AI Engine library blocks.
Additionally, the tool lets you use a combination of AI Engine and programmable logic (HDL/HLS) blocks to create and simulate a design. By seamlessly integrating Vitis Model Composer AI Engine blocks with Simulink source and sink blocks, simulation results may be viewed.
For usage in the Simulink environment, Vitis Model Composer offers a collection of blocks that are optimized for speed. These consist of:
AI Engine blocks
Image Credit To AMD
Comprises a collection of intricate AI Engine DSP building elements pertaining to mixers, FIR, FFT, and DDS.
includes blocks for importing graphs and kernels that may be directed to Versal devices’ AI Engine section.
HLS (Targeting PL and generates HLS code)
Targeting PL and producing HLS code, HLS provides preset blocks that contain bit-wise operations, logic, linear algebra, and math functional blocks.
Block the import of HLS kernels that are intended for Versal devices’ PL section.
HDL (Produces RTL code and targets PL)
Blocks for modeling and synthesizing DSP, arithmetic, and logic components on an FPGA
contains a FIR Compiler block that targets the Versal design’s specific DSP48E1 and DSP48E2 hardware resources.
Blocks that facilitate communication between the AMD HDL blockset and the AI Engine.
Unleash DSP Compute with AMD Versal AI Engines
For next-generation DSP workloads, speed up demanding high-performance DSP applications.
AMD Versal AI Engine Technology Enables High-Performance Digital Signal Processing (DSP) Requirements
Clients developing next-generation DSP applications need enormous computational power, which conventional FPGA designs cannot effectively provide. Large quantities of DSP blocks and programmable logic resources may be used by compute-intensive DSP applications like FIR, FFT, and General Matrix Multiply.
The total computation capability that conventional programmable logic devices may provide may be greatly diminished by this need. For demanding DSP workloads with stringent power constraints, just expanding the number of DSP blocks and programmable logic available is not a scalable solution.
In these situations, Versal AI Engines are intended to provide a more effective computing solution.
Boost Compute and Use Less Power
Optimize performance and transform your DSP designs.
Did you know that you may increase scalability and efficiency to satisfy the growing needs of high-performance, next-generation DSP applications? Learn 5 strategies to improve your DSP designs using AMD Versal AI Engines.
Access Benchmarks Comparing Versal AI Engines to Previous Programmable Logic Technology
Please get in touch with sales or your FAE for test results and source designs for head-to-head benchmark comparisons between designs that use just Programmable Logic and adaptable SoC + AI Engine designs that use AMD Versal adaptable SoCs.
Get Started with Versal AI Engines for DSP
Increase DSP compute density for the next generation of demanding DSP workloads by speeding up the most demanding high-performance DSP applications.
Read more on govindhtech.com
#AMDVersalAIEngine#PoweringNextGenIntelligence#AIEngine#FPGA#AMDVersal#KeyFeatures#AMD#DesigningAMD#AIEngineblocks#DSPCompute#technology#technews#news#govindhtech
2 notes
·
View notes